Connecting to Okta Using OAuth 2.0
About Okta
Okta is an emerging platform that manages online identities for enterprises. Integration with AtScale will provide you with:
- A single source of truth for user's information
- Instantaneous user disablement from the Okta interface
- Entitlement grants from within Okta
When to Leverage AtScale's Okta Integration
AtScale recommends using Okta when your organization leverages their platform for all of their applications in place of an LDAP server. While there are different mechanisms to integrate with Okta, you can leverage their LDAP server. AtScale provides integration with the OAuth 2.0 mechanism for middleware.
Overview
- Create a public and private key (JWKS Token) that Okta will use to communicate.
- Create an Administrator Okta API token that will be used to create an AtScale service.
- Create the OAuth Service Application by combining the JWKS token (public key) and the Administrator Okta Application API token. Send the public key to AtScale.
- Grant permissions to the AtScale service within Okta.
- Revoke the Okta API token.
- Configure AtScale with the private key pair and the Okta service key
- Assign users to the AtScale service within Okta.
Procedure
-
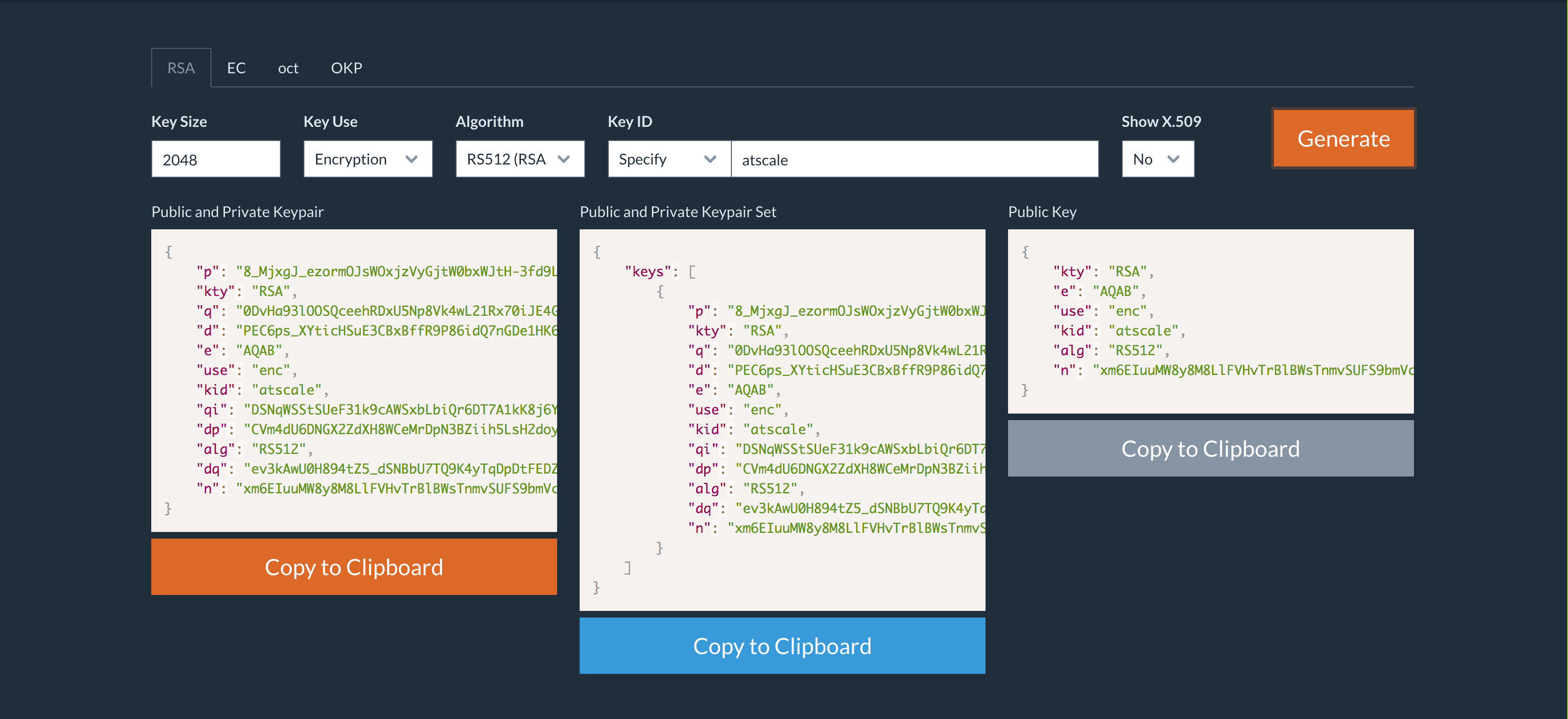
Create a public and private key using the JWKS token generator here. AtScale will use the Public Key generated from this step.
- Key size: 2048
- Key use: signature
- Algorithm: RSA256
- Key ID (Optional): This can be any value.
- Show X509: No
Figure 1. An example JWKS token. Save both the Public and Private Keypair (left-hand image), and the Public Key (right-most image).
-
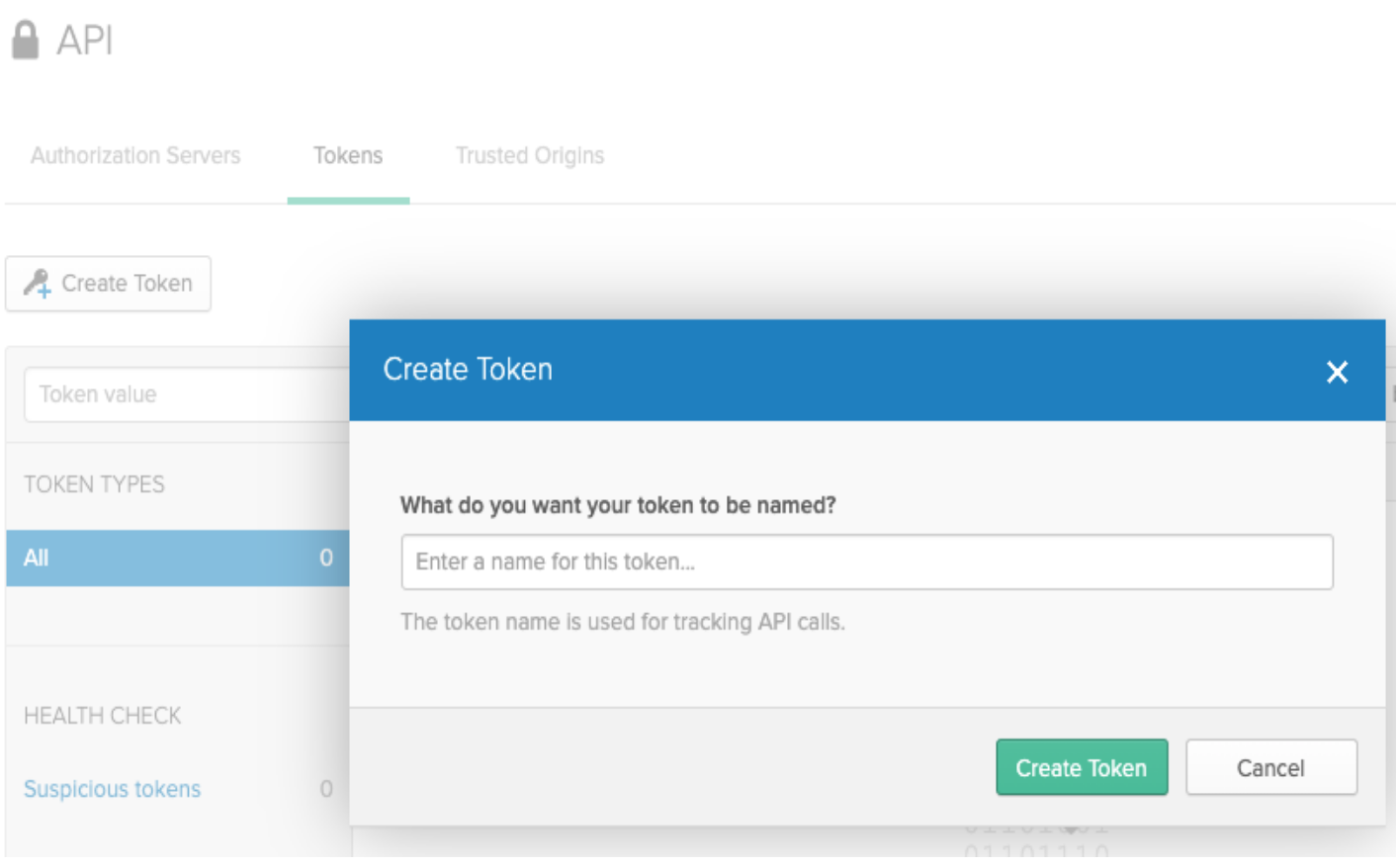
Create an Administrator Okta Application API token.
- Sign in to Okta as an Administrator.
- Select API > Tokens and then enter a unique name for your token. This API token will be revoked later in this procedure.
- Save the resulting SSWS token for later use.
Figure 2. The Create Token dialog from within an Okta application.
-
Create an OAuth Service App by combining the JWKS token and the Administrator Okta Application API token. You will send a CURL request to the Okta API requesting to use the JWKS token. The response will contain a new client ID. Additional information about this step may be obtained in the Okta documentation here.
-
Modify the following parameters in the CURL request (see Figure 3):
-
Replace the
${api_token}with the Okta Application API token created in Step 2. Ensure to leave the SSWS prefix. -
Replace the example public key with the public key created in Step 1 (See Figure 1).
-
Replace
https://${yourOktaDomain}/oauth2/v1/clientswith your Okta subdomain. Be sure to point to the subdomain and not to the admin URL.Figure 3. an example CURL request.
curl -X POST \
-H 'Accept: application/json' \
-H "Authorization: SSWS ${api_token}" \
-H 'Content-Type: application/json' \
-d ' {
"client_name": "AtScale Client",
"response_types": [
"token"
],
"grant_types": [
"client_credentials"
],
"token_endpoint_auth_method": "private_key_jwt",
"application_type": "service",
"jwks": {
"keys": [
{
"kty": "RSA",
"e": "AQAB",
"use": "sig",
"kid": "O4O",
"alg": "RS256",
"n": "u<example>w"
}
]
}
}' "https://${yourOktaDomain}/oauth2/v1/clients"Figure 4. An example response from a modified CURL request:
-
Attention: Take note of the client_id. This string is required to Configure the AtScale Directory setup in later steps.
"jwks": {
"keys": [
{
"kty": "RSA",
"alg": "RS256",
"kid": "AtScale",
"use": "sig",
"e": "AQAB",
"n": "<example>"
}
]
},
"client_id": "<SAVE THIS ID>",
"client_id_issued_at": 1602184770,
"client_name": "AtScale Client",
"client_uri": null,
"logo_uri": null,
"redirect_uris": [],
"response_types": [
"token"
],
"grant_types": [
"client_credentials"
],
"token_endpoint_auth_method": "private_key_jwt",
"application_type": "service"
-
Grant permissions to AtScale from within the Okta Application
-
From within Okta, select Applications. You should have a new application named AtScale Client created from the previous step.
-
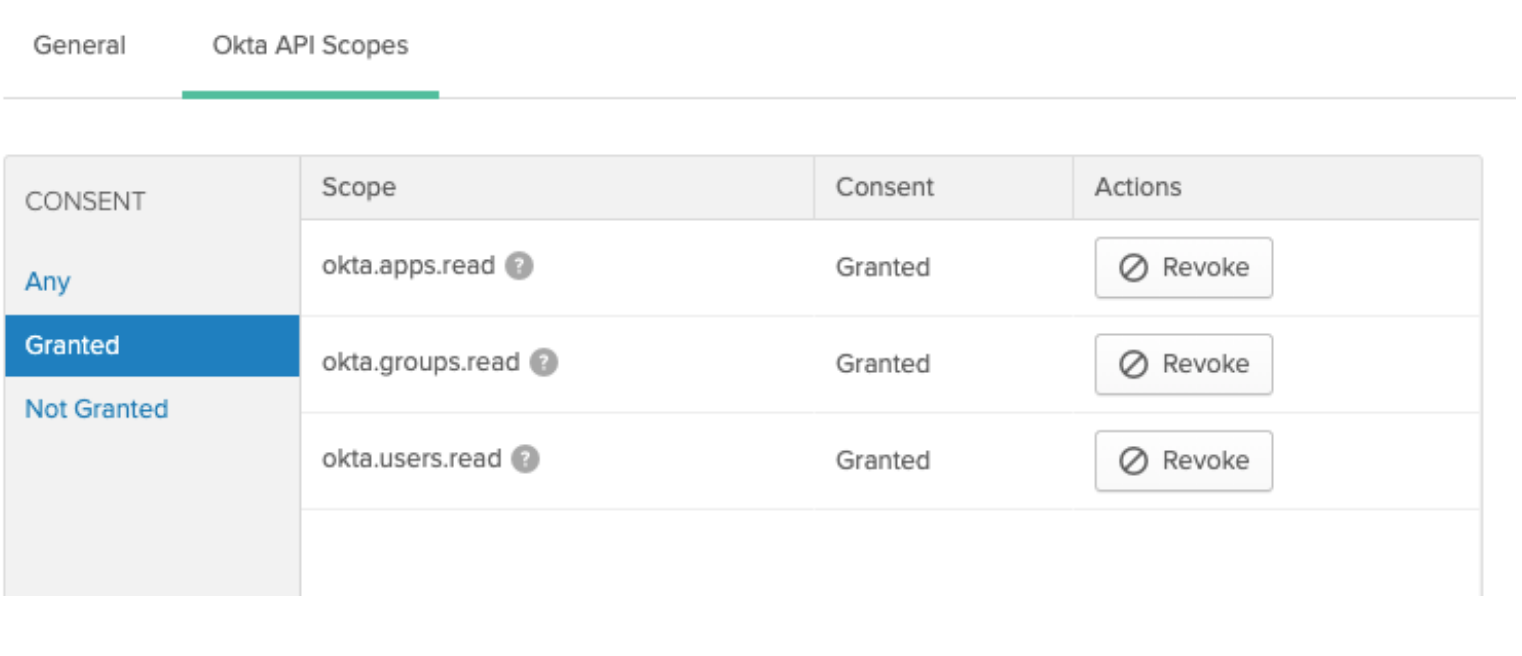
Select the Okta API Scopes tab. Grant the following Okta grants to your application.
okta.apps.readokta.groups.readokta.users.read
-
Once complete, select the Granted tab within Okta to ensure that the correct scopes were added.
Figure 5. The Granted tab displaying the requisite Okta scopes.
-
-
Revoke the API token generated in Step 2.
- In Okta Select API > Tokens and then select the trash button to revoke the API token.
-
Configure AtScale with the private key pair and the Okta service key.
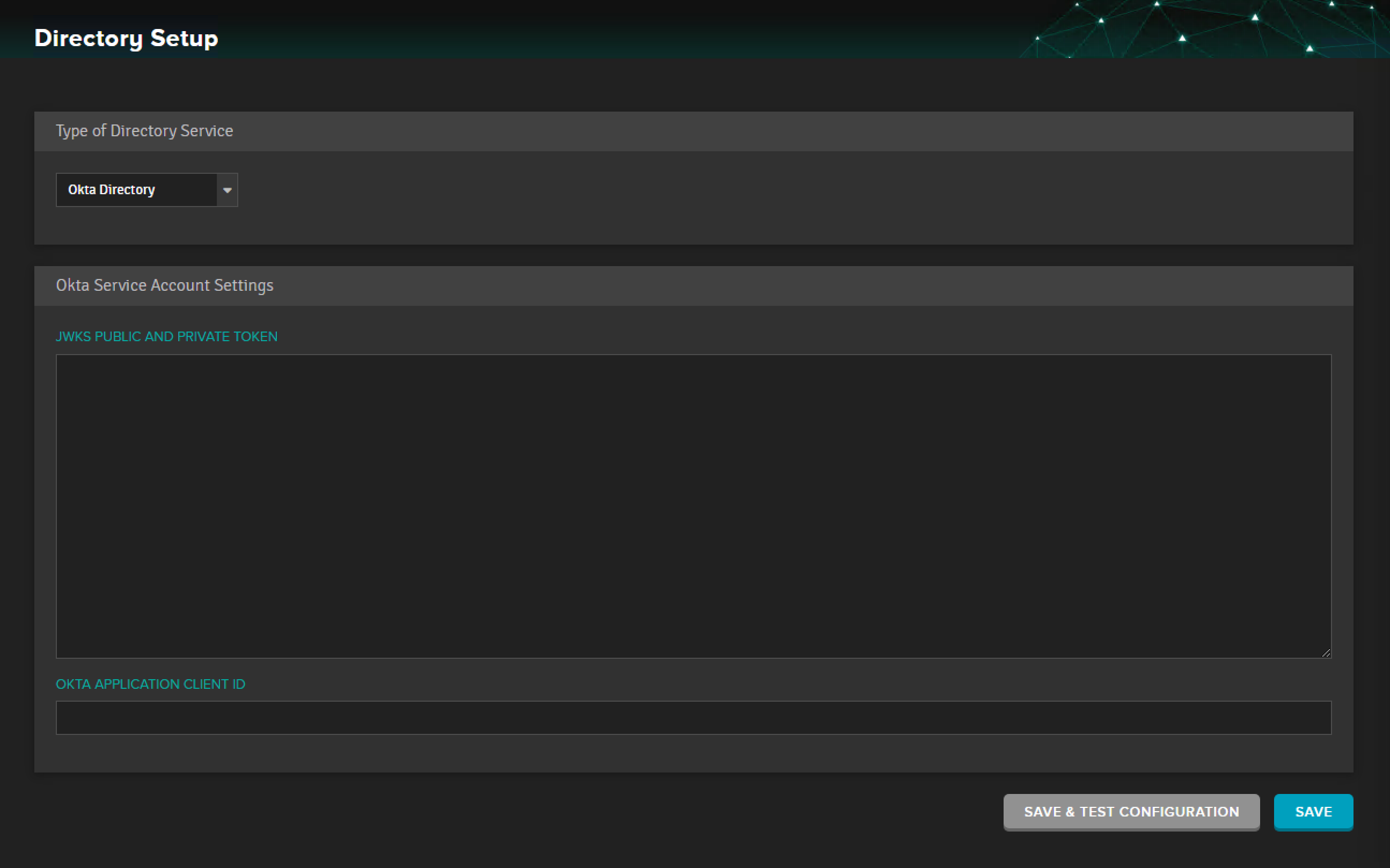
- In AtScale, select Security > Directory: Setup. Select the drop-down beneath Type of Directory Service and select Okta Directory.
- Input the Okta Application Client ID (The client_id from Step 3, Figure 4) into the corresponding field in AtScale.
- Insert the JWKS Public and Private Key Tokens generated from the step 1 (The left-most field from Figure 1) into the corresponding fields in AtScale.
- Select Save and Test Configuration to test that the configuration was valid. Select Save to save the valid AtScale/Okta configuration.
Figure 5. The Okta Directory setup page within AtScale.
-
Assign users to the AtScale service within Okta.